AWS VPC endpoints AKA AWS PrivateLink
A VPC endpoint enables connections between a virtual private cloud (VPC) and supported services, without requiring that you use an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. Therefore, your VPC is not exposed to the public internet.
You can use Amazon VPC to define a virtual private cloud (VPC), which is a logically isolated virtual network. You can launch AWS resources in your VPC. You can allow the resources in your VPC to connect to resources outside that VPC. For example, add an internet gateway to the VPC to allow access to the internet, or add a VPN connection to allow access to your on-premises network. Alternatively, use AWS PrivateLink to allow the resources in your VPC to connect to services in other VPCs using private IP addresses, as if those services were hosted directly in your VPC.
The following diagram provides a high-level overview of how AWS PrivateLink works. Service consumers create interface VPC endpoints to connect to endpoint services that are hosted by service providers.
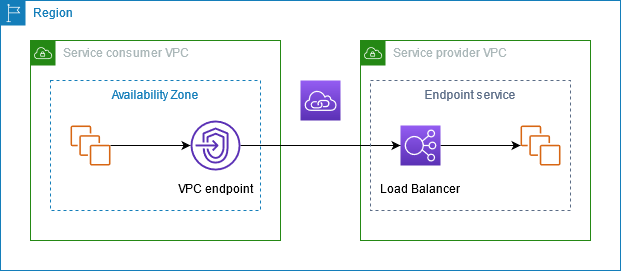
Service providers
The owner of a service is the service provider. Service providers include AWS, AWS Partners, and other AWS accounts. Service providers can host their services using AWS resources, such as EC2 instances, or using on-premises servers.
Endpoint services
A service provider creates an endpoint service to make their service available in a Region. A service provider must specify a load balancer when creating an endpoint service. The load balancer receives requests from service consumers and routes them to your service.
By default, your endpoint service is not available to service consumers. You must add permissions that allow specific AWS principals to connect to your endpoint service.
Service names
Each endpoint service is identified by a service name. A service consumer must specify the name of the service when creating a VPC endpoint. Service consumers can query the service names for AWS services. Service providers must share the names of their services with service consumers.
Service states
The following are the possible states for an endpoint service:
Pending– The endpoint service is being created.Available– The endpoint service is available.Failed– The endpoint service could not be created.Deleting– The service provider deleted the endpoint service and deletion is in progress.Deleted– The endpoint service is deleted.
Service consumers
The user of a service is a service consumer. Service consumers can access endpoint services from AWS resources, such as EC2 instances, or from on-premises servers.
VPC endpoints
A service consumer creates a VPC endpoint to connect their VPC to an endpoint service. A service consumer must specify the service name of the endpoint service when creating a VPC endpoint. There are multiple types of VPC endpoints. You must create the type of VPC endpoint that’s required by the endpoint service.
Interface– Create an interface endpoint to send traffic to endpoint services that use a Network Load Balancer to distribute traffic. Traffic destined for the endpoint service is resolved using DNS.GatewayLoadBalancer– Create a Gateway Load Balancer endpoint to send traffic to a fleet of virtual appliances using private IP addresses. You route traffic from your VPC to the Gateway Load Balancer endpoint using route tables. The Gateway Load Balancer distributes traffic to the virtual appliances and can scale with demand.Gateway– Create a gateway endpoint to send traffic to Amazon S3 or DynamoDB using private IP addresses. You route traffic from your VPC to the gateway endpoint using route tables. Gateway endpoints do not enable AWS PrivateLink.
Endpoint network interfaces
An endpoint network interface is a requester-managed network interface that serves as an entry point for traffic destined to an endpoint service. For each subnet that you specify when you create a VPC endpoint, we create an endpoint network interface in the subnet.
If a VPC endpoint supports IPv4, its endpoint network interfaces have IPv4 addresses. If a VPC endpoint supports IPv6, its endpoint network interfaces have IPv6 addresses. The IPv6 address for an endpoint network interface is unreachable from the internet. If you describe an network interface with an IPv6 address, notice that denyAllIgwTraffic is enabled.
The IP addresses of an endpoint network interface will not change during the lifetime of its VPC endpoint.
Endpoint policies
A VPC endpoint policy is an IAM resource policy that you attach to a VPC endpoint. It determines which principals can use the VPC endpoint to access the endpoint service. The default VPC endpoint policy allows all actions by all principals on all resources over the VPC endpoint.
Endpoint states
When you create a VPC endpoint, the endpoint service receives a connection request. The service provider can accept or reject the request. If the service provider accepts the request, the service consumer can use the VPC endpoint after it enters the Available state.
The following are the possible states for a VPC endpoint:
PendingAcceptance– The connection request is pending. This is the initial state if requests are manually accepted.Pending– The service provider accepted the connection request. This is the initial state if requests are automatically accepted. The VPC endpoint returns to this state if the service consumer modifies the VPC endpoint.Available– The VPC endpoint is available for use.Rejected– The service provider rejected the connection request. The service provider can also reject a connection after it is available for use.Expired– The connection request expired.Failed– The VPC endpoint could not be made available.Deleting– The service consumer deleted the VPC endpoint and deletion is in progress.Deleted– The VPC endpoint is deleted.
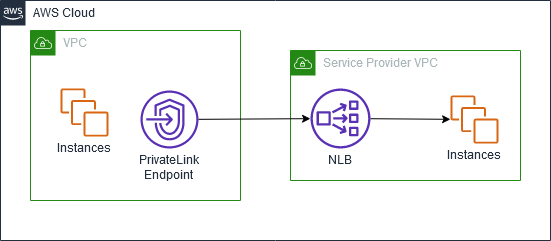
AWS PrivateLink connections
Traffic from your VPC is sent to an endpoint service using a connection between the VPC endpoint and the endpoint service. Traffic between a VPC endpoint and an endpoint service stays within the AWS network, without traversing the public internet.
A service provider adds permissions so that service consumers can access the endpoint service. The service consumer initiates the connection and the service provider accepts or rejects the connection request.
With interface VPC endpoints, service consumers can use endpoint polices to control which IAM principals can use a VPC endpoint to access an endpoint service.
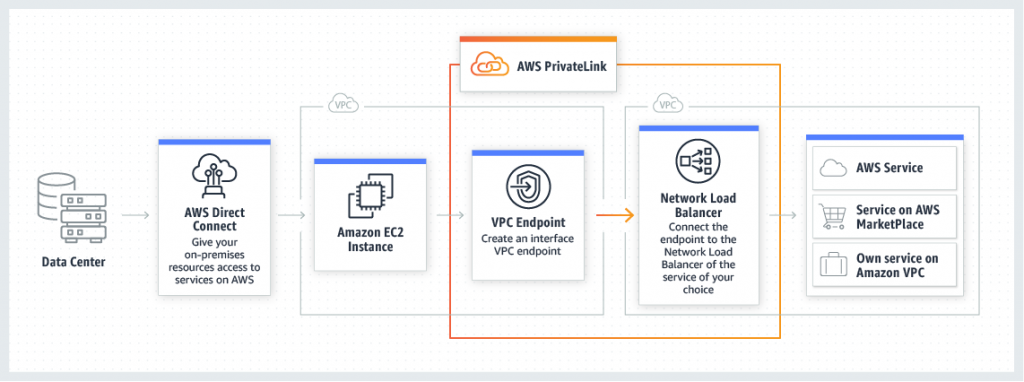
AWS VPC endpoint services AKA AWS PrivateLink-powered service
You can create your own application in your VPC and configure it as an AWS PrivateLink-powered service (referred to as an endpoint service). Other AWS principals can create a connection from their VPC to your endpoint service using an interface VPC endpoint or a Gateway Load Balancer endpoint, depending on the type of service. You are the service provider, and the AWS principals that create connections to your service are service consumers.
Endpoint services require either a Network Load Balancer or a Gateway Load Balancer. The load balancer receives requests from service consumers and routes them to your service. In this case, you’ll create an endpoint service using a Network Load Balancer.
AWS PrivateLink Design Diagram
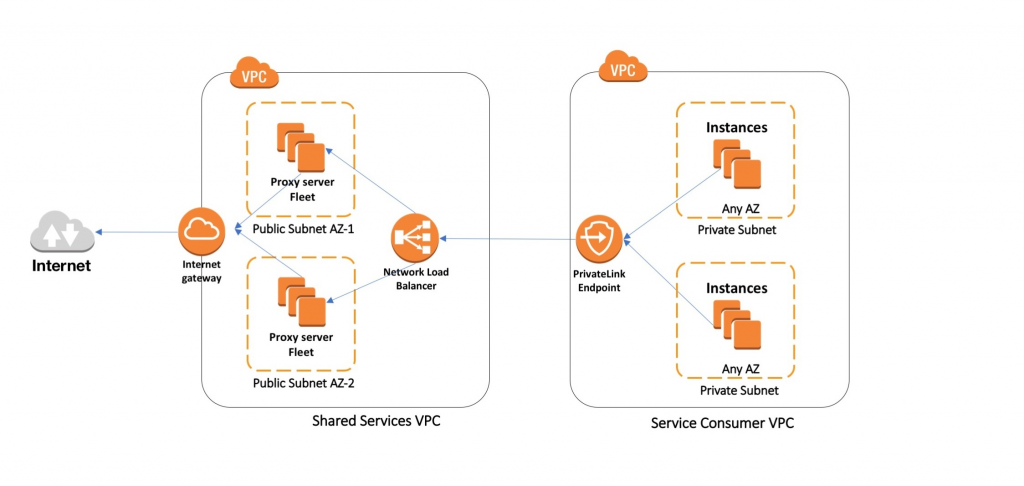
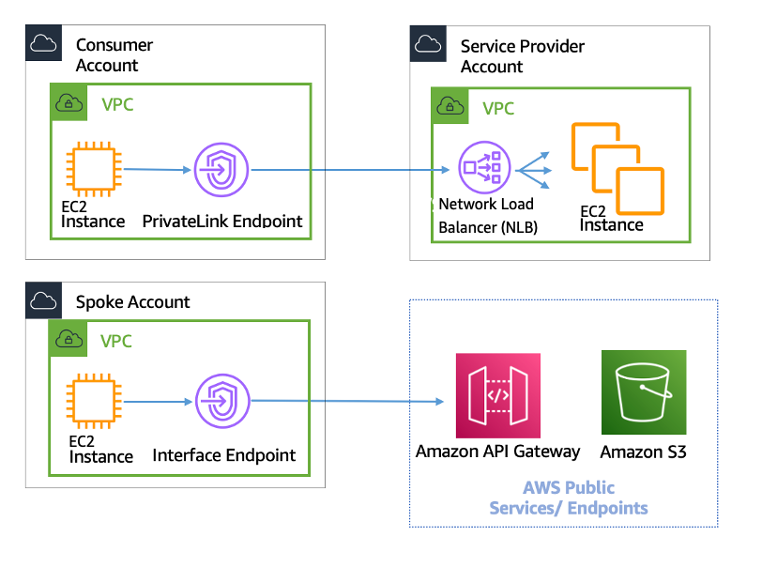
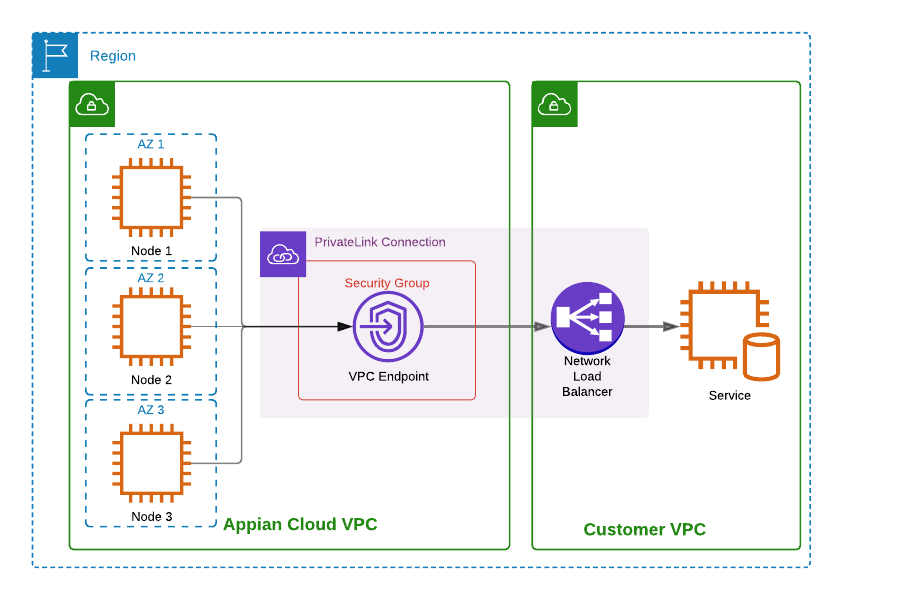
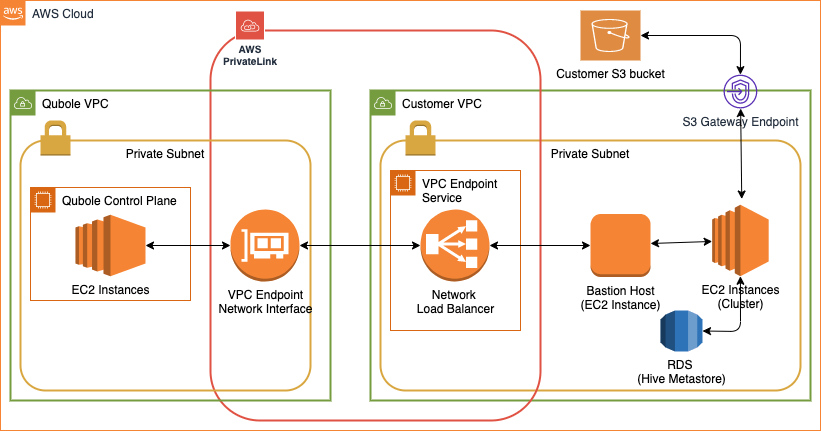
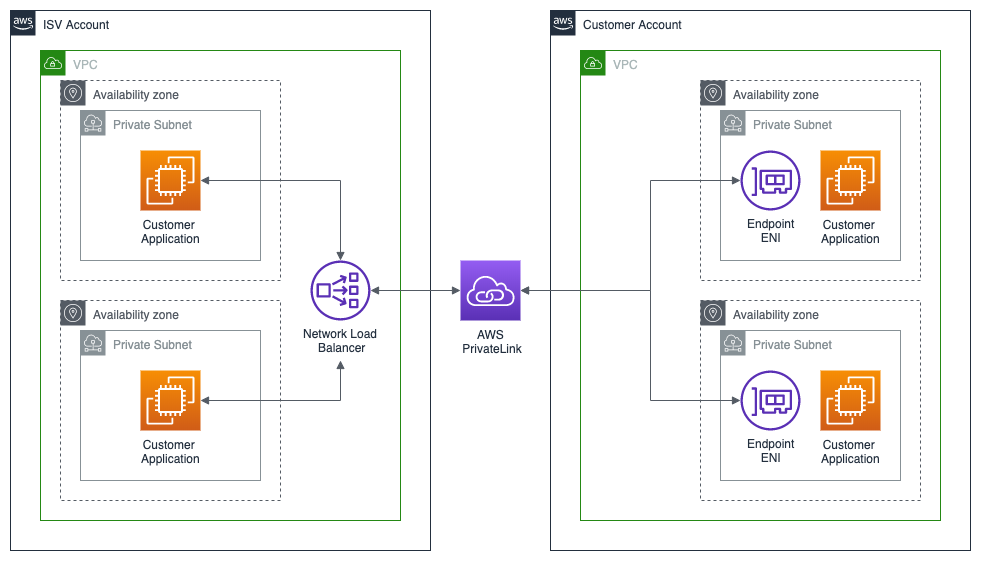
Differnece Between AWS Private Link vs VPC Endpoint
VPC endpoint — The entry point in your VPC that enables you to connect privately to a service.
AWS PrivateLink — A technology that provides private connectivity between VPCs and services.
So PrivateLink is technology allowing you to privately (without Internet) access services in VPCs. These services can be your own, or provided by AWS.
Let’s say that you’ve developed some application and you are hosting it in your VPC. You would like to enable access to this application to services in other VPCs and other AWS users/accounts. But you don’t want to setup any VPC peering nor use Internet for that. This is where PrivateLink can be used. Using PrivateLink you can create your own VPC endpoint services which will enable other services to use your application.
In the above scenario, VPC interface endpoint is a resource that users of your application would have to create in their VPCs to connect to your application. This is same as when you create VPC interface endpoint to access AWS provided services privately (no Internet), such as Lambda, KMS or SMS.
To sum up, PrivateLink is general technology which can be used by you or AWS to allow private access to internal services. VPC interface endpoint is a resource that the users of such VPC services create in their own VPCs to interact with them.
Different between AWS VPC endpoints and aws VPC endpoint services
AWS VPC (Virtual Private Cloud) endpoints and AWS VPC endpoint services are two different concepts in AWS networking.
An AWS VPC endpoint is a logical entity that enables direct access to AWS services over a private connection within a VPC. It allows you to privately connect your VPC to supported AWS services without using an Internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. VPC endpoints are secure, scalable, and highly available, and they allow you to access AWS services using private IP addresses from your VPC.
An AWS VPC endpoint service, on the other hand, is a service that you create and manage to receive traffic from one or more VPCs. It is essentially a target for VPC endpoint connections. When you create an endpoint service, you specify which VPCs can connect to the service and which network load balancer to use for the endpoint connections. You can also configure policies to control which resources can be accessed by the endpoint connections.
In summary, an AWS VPC endpoint is a connection that allows you to access AWS services over a private connection within a VPC, while an AWS VPC endpoint service is a service that you create to receive traffic from VPCs through VPC endpoints.
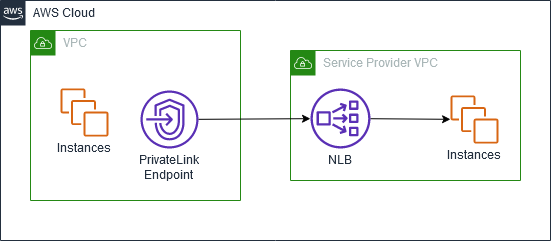
Example of AWS Private Link & VPC Endpoint Implementations
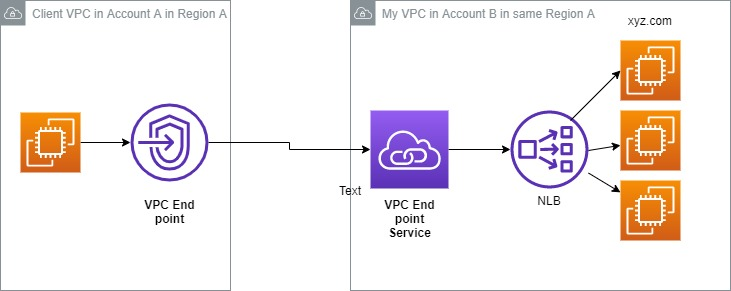
Suppose there is a website xyz.com that I am hosting in a bunch of Ec2 instances, exposed to the outside world thru a Network load balancer. Now, a client who has his/her own AWS account, wants to access this xyz.com from an Ec2 running in their aws account.
One approach is to go thru the Internet. However the client wants to avoid the internet route. He/she wants to use the AWS backbone to reach xyz.com. The technology that enables that, is AWS Private link. (note that if you search for Private Link in the AWS services, there will be none. You will get “End point services” as the closest hit)
So, this is how to route traffic through the AWS backbone:
- I, the owner of xyz.com, will create a VPC End Point Service (NOTE the keyword Service here) The VPC End point service will point to my Network load balancer. I will then give my VPC End point service name to the client.
- The client will create a VPC End Point (NOTE.. this is different from #1). While creating it, the client will specify the VPC End Point Service name (from #1) that he got from me.
- I can choose to be prompted to accept the connection from the client to my VPC End point service. As soon as I accept it, then the client can reach xyz.com from his/her EC2 instance. There is no Internet, no direct connect or VPN.. this simply works; and its secure. And which technology enabled it.. AWS Private link !!!
PRIVATE LINK IS THE ONLY TECHNOLOGY THAT ALLOWS 2 VPCS TO CONNECT THAT HAVE OVERLAPPING CIDR RANGES.
How to setup Private Link in AWS using Endpoint and Endpoint Services
https://docs.aws.amazon.com/vpc/latest/privatelink/create-endpoint-service.html
Reference
- AWS PrivateLink concepts – Amazon Virtual Private Cloud
- Create a service powered by AWS PrivateLink – Amazon Virtual Private Cloud
- https://docs.aws.amazon.com/whitepapers/latest/aws-privatelink/what-are-vpc-endpoints.html
- Create a service powered by AWS PrivateLink – Amazon Virtual Private Cloud
- Apache Lucene Query Example - April 8, 2024
- Google Cloud: Step by Step Tutorials for setting up Multi-cluster Ingress (MCI) - April 7, 2024
- What is Multi-cluster Ingress (MCI) - April 7, 2024

