
What is Hashicorp Boundary?
Hashicorp Boundary was introduced by Hashicorp company as Simple and secure remote access.
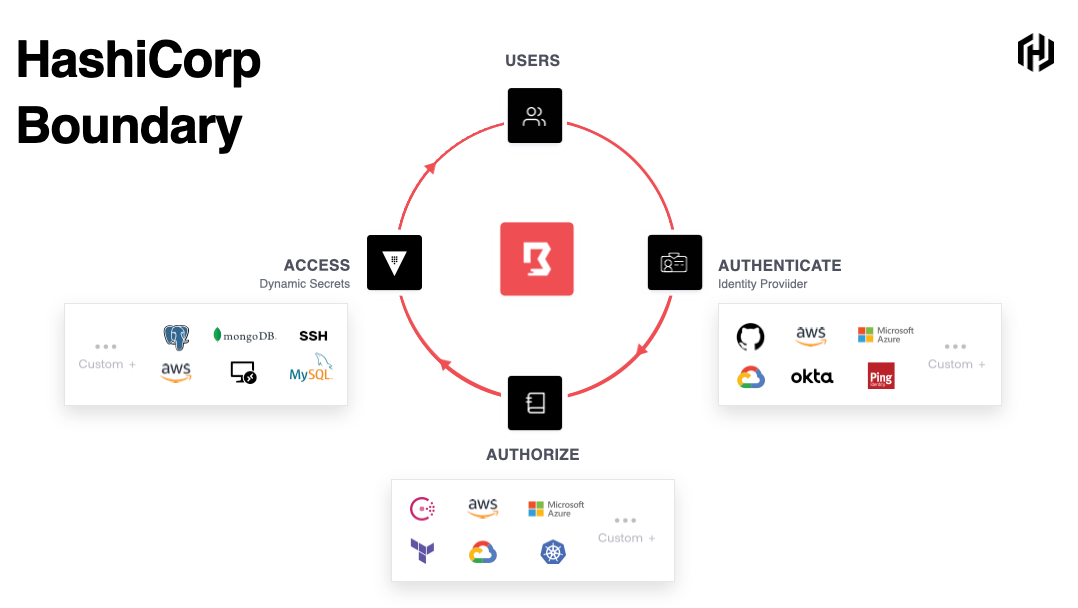
HashiCorp Boundary is a secure remote access solution that provides an easy way to allow access to hosts and critical systems with fine-grained authorizations based on trusted identities.
Boundary is designed to grant access to critical systems using the principle of least privilege, solving challenges organizations had to face when users need to securely access applications and machines.
Traditional products that grant access to systems are cumbersome, painful to maintain, or are black boxes lacking extensible APIs.
Boundary allows authenticated and authorized users to access secure systems in private networks without granting access to the larger network where those systems reside.
What is the use of Hashicorp Boundary?
- Identity-based access for zero trust security – Configure identity-based access conrols for your infrastructure, wherever it resides.
- Compliance without over-head – Provide session visibility that enables team to stay compliant.
- Fully integrated secrets management – Just in time credentials from vault for SSO to critical infrastructure targets.
List of Hashicorp Boundary Certification
There is no official certification of Hashicorp boundary right now.
Hashicorp Boundary Certification path
As mentioned above there is no official certification from Hashicorp but still you can become Boundary certified professional by getting certified from DevOpsSchool and ScmGalaxy institute.
Best Hashicorp Boundary Certification Tutorials
https://learn.hashicorp.com/collections/boundary/getting-started
Best Hashicorp Boundary Certification Video Tutorials
- Mastering Qualitative Research: The Role of Focus Groups in Data Collection - July 11, 2024
- What is robots ops? - July 10, 2024
- 5 Effective Online Learning Strategies for DevOps Professionals - July 4, 2024

