
1. What is kubehunter?
Kubehunter is a tool used to scan Kubernetes clusters for security vulnerabilities.
2. What are some common security vulnerabilities in Kubernetes clusters?
Some common vulnerabilities include exposed dashboards, weak authentication, and outdated software.
3. How do you use kubehunter?
You can use kubehunter by running the command “kubehunter scan”.
4. What is the output of a kubehunter scan?
The output of a kubehunter scan includes a list of vulnerabilities found in the Kubernetes cluster.
5. How do you fix vulnerabilities found by kubehunter?
You can fix vulnerabilities found by kubehunter by following the recommended steps provided in the scan output.
6. What is a Kubernetes pod?
A Kubernetes pod is the smallest deployable unit in a Kubernetes cluster.
7. What is a Kubernetes deployment?
A Kubernetes deployment is a way to manage the deployment of pods in a Kubernetes cluster.
8. What is a Kubernetes service?
A Kubernetes service is a way to expose a deployment to the outside world.
9. What is a Kubernetes namespace?
A Kubernetes namespace is a way to group resources in a Kubernetes cluster.
10. What is a Kubernetes config map?
A Kubernetes config map is a way to store configuration data in a Kubernetes cluster.
11. What is a Kubernetes secret?
A Kubernetes secret is a way to store sensitive data in a Kubernetes cluster.
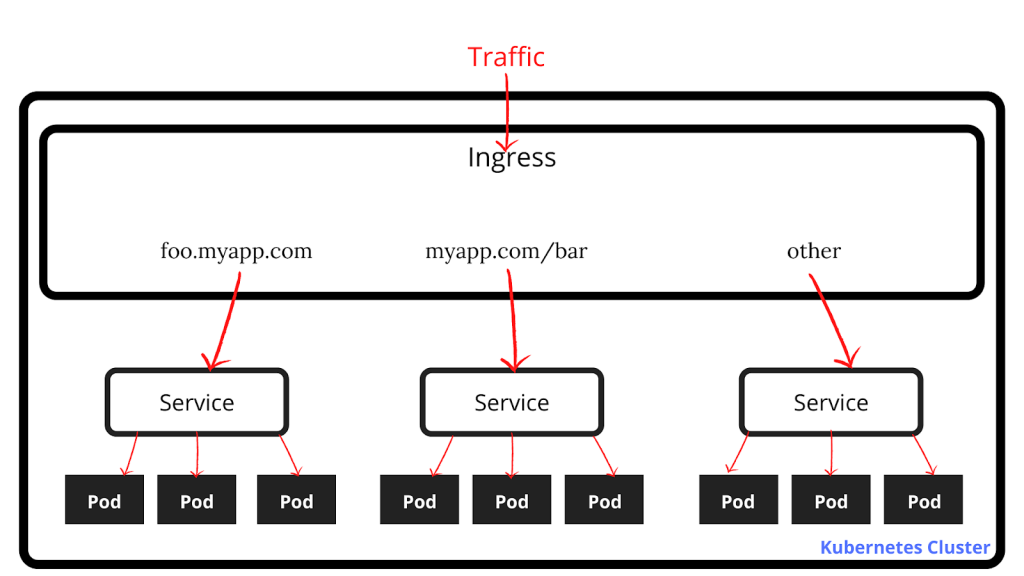
12. What is a Kubernetes ingress?
A Kubernetes ingress is a way to route traffic to different services in a Kubernetes cluster.
13. What is a Kubernetes node?
A Kubernetes node is a physical or virtual machine that runs pods in a Kubernetes cluster.
14. What is a Kubernetes cluster?
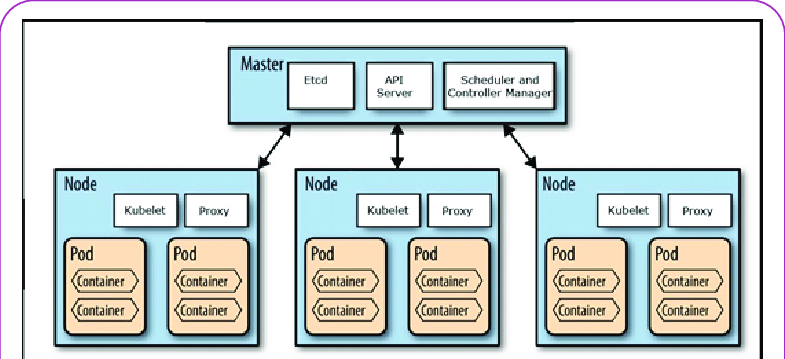
A Kubernetes cluster is a group of nodes that work together to run applications in containers.
15. What is a container?
A container is a lightweight, standalone executable package that contains everything needed to run an application.
16. What is Docker?
Docker is a platform for building, shipping, and running containers.
17. What is Kubernetes?
Kubernetes is an open-source platform for managing containerized workloads and services.
18. What is a container image?
A container image is a lightweight, standalone, and executable package that contains everything needed to run an application.
19. What is a container registry?
A container registry is a place to store and distribute container images.
20. What is a container orchestration platform?
A container orchestration platform is a tool used to manage the deployment, scaling, and operation of containers.
21. What is a microservice?
A microservice is a small, independent, and loosely coupled service that performs a specific task.
22. What is a monolithic application?
A monolithic application is a single, large, and tightly coupled application that performs multiple tasks.
23. What is a load balancer?
A load balancer is a tool used to distribute traffic across multiple servers.
24. What is a reverse proxy?
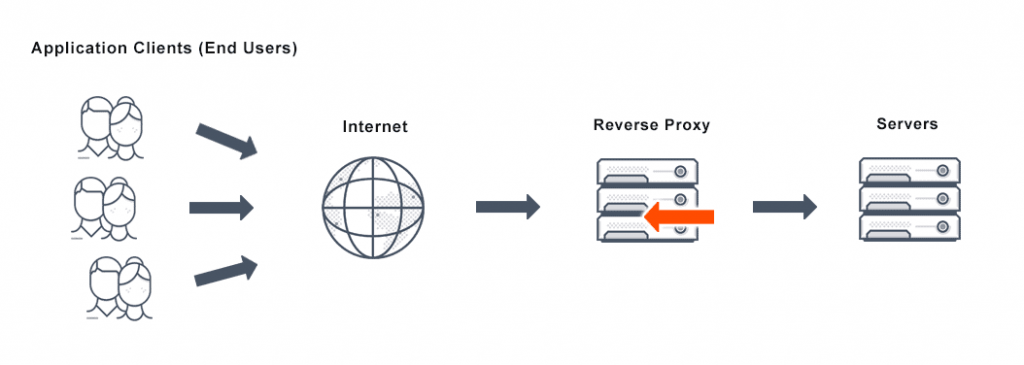
A reverse proxy is a tool used to route traffic from the internet to a specific server.
25. What is a firewall?
A firewall is a tool used to block unauthorized access to a network.
26. What is a VPN?
A VPN is a tool used to create a secure connection between two networks over the internet.
27. What is encryption?
Encryption is a tool used to protect data by converting it into a secret code.
28. What is decryption?
Decryption is a tool used to convert encrypted data back into its original form.
29. What is a certificate?
A certificate is a digital document used to verify the identity of a person, organization, or website.
30. What is SSL?
SSL is a tool used to encrypt data sent between a website and a user’s browser.
31. What is TLS?
TLS is a tool used to encrypt data sent between a website and a user’s browser.
32. What is a vulnerability?
A vulnerability is a weakness in a system that can be exploited by an attacker.
33. What is an exploit?
An exploit is a tool used to take advantage of a vulnerability in a system.
34. What is a patch?
A patch is a software update that fixes a vulnerability in a system.
35. What is a vulnerability scanner?
A vulnerability scanner is a tool used to scan a system for vulnerabilities.
36. What is a penetration test?
A penetration test is a simulated attack on a system to identify vulnerabilities.
37. What is a threat model?
A threat model is a way to identify potential threats to a system and develop strategies to mitigate them.
38. What is a risk assessment?
A risk assessment is a way to identify potential risks to a system and develop strategies to mitigate them.
39. What is a security policy?
A security policy is a set of rules and guidelines that define how a system should be secured.
40. What is a security audit?
A security audit is a review of a system’s security to identify potential vulnerabilities.
41. What is a security incident?
A security incident is an event that compromises the security of a system.
42. What is a security breach?
A security breach is an unauthorized access to a system.
43. What is a security incident response plan?
A security incident response plan is a plan that outlines the steps to be taken in the event of a security incident.
44. What is a security awareness program?
A security awareness program is a program that educates users on how to identify and prevent security threats.
45. What is a security control?
A security control is a tool or process used to mitigate security risks.
46. What is a security risk?
A security risk is a potential threat to the security of a system.
47. What is a security threat?
A security threat is an event or action that poses a risk to the security of a system.
48. What is a security vulnerability?
A security vulnerability is a weakness in a system that can be exploited by an attacker.
49. What is a security incident response team?
A security incident response team is a team responsible for responding to security incidents.
50. What is a security clearance?
A security clearance is a process used to determine if a person is eligible for access to classified information.
Related video:
- Degree Pursuit: Navigating the Path to Educational Excellence - July 4, 2024
- Why Is Studying English Important in a Business Environment? - July 4, 2024
- Top 10 Data Science Skills You Need in 2024 - July 3, 2024

