
eBPF, which stands for “extended Berkeley Packet Filter,” is a powerful and flexible technology used in modern Linux kernels for various purposes, including networking, monitoring, and security. Originally inspired by the traditional Berkeley Packet Filter (BPF), eBPF extends its capabilities and provides a safe and efficient way to run custom code within the Linux kernel.
eBPF, or Extended Berkeley Packet Filter, is a technology that allows users to run sandboxed programs in the Linux kernel. It is a powerful tool that can be used for a variety of tasks, including:
- Observability: eBPF can be used to collect detailed metrics and tracing data from the kernel. This data can be used to troubleshoot performance problems, debug applications, and monitor system health.
- Security: eBPF can be used to implement security features such as firewalls, intrusion detection systems, and load balancers. It can also be used to isolate malicious processes and protect the system from attacks.
- Networking: eBPF can be used to implement custom networking features such as traffic shaping, load balancing, and filtering. It can also be used to improve the performance of existing networking protocols.
eBPF is still under development, but it is already being used by a wide range of companies and organizations, including Google, Netflix, and Cloudflare.
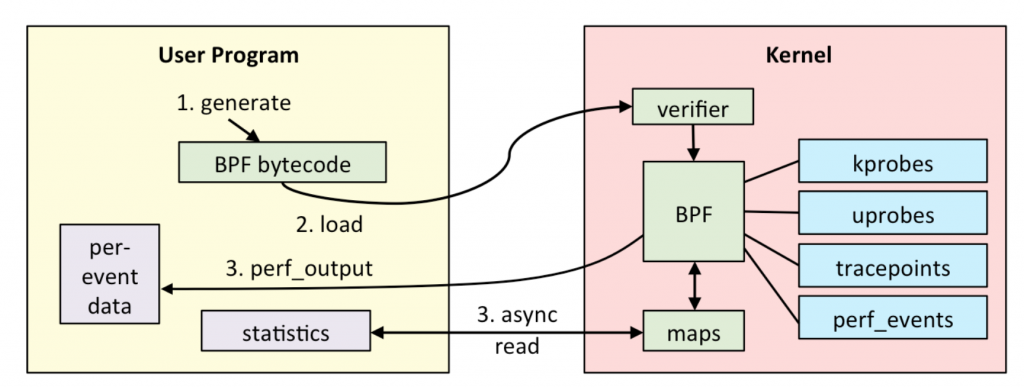
Benefits of using eBPF
- Performance: eBPF programs are compiled to native machine code, so they can run very efficiently. This is important for applications that need to process large amounts of data or perform time-critical tasks.
- Safety: eBPF programs are verified by the kernel before they are allowed to run. This helps to prevent them from crashing the system or causing other problems.
- Flexibility: eBPF programs can be used to implement a wide range of functionality, from simple tasks like filtering network traffic to complex tasks like monitoring system performance.
eBPF is a powerful and versatile tool that can be used to improve the performance, security, and observability of Linux systems.
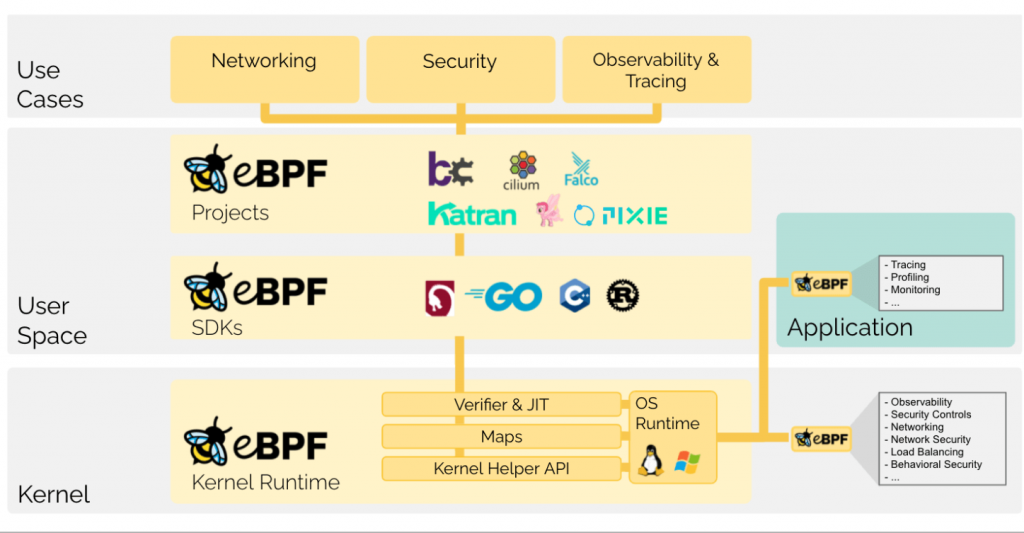
Key aspects and use cases of eBPF
- Programmable Kernel: eBPF allows developers to write custom programs (called eBPF programs) that can be loaded and executed within the Linux kernel. These programs can interact with various kernel subsystems without requiring kernel module recompilation or reloading.
- Networking: eBPF is extensively used in networking for packet filtering, monitoring, and load balancing. It enables the creation of custom packet processing logic, making it possible to implement complex network functions efficiently, such as firewalls, traffic shaping, and packet capture.
- Tracing and Monitoring: eBPF is commonly used for dynamic tracing and monitoring of system and application behavior. Tools like BPFTrace and perf use eBPF to collect detailed insights into system performance, function execution, and resource utilization.
- Security: eBPF is a valuable tool for enhancing the security of Linux systems. It can be used to create custom security policies, detect malicious activities, and implement security-related functions, such as seccomp (sandboxing) and audit mechanisms.
- Observability: eBPF enables deep observability of the Linux kernel and user-space applications. It can collect and analyze various types of telemetry data, such as system calls, function traces, and network events, which is essential for diagnosing performance issues and troubleshooting problems.
- Efficiency: eBPF programs are designed to be efficient and safe. They are executed within a restricted environment, ensuring that they cannot crash the kernel or introduce security vulnerabilities. eBPF programs are also just-in-time (JIT) compiled to native code for high performance.
- User-Space Integration: eBPF programs can communicate with user-space applications through various mechanisms, such as maps (key-value stores), allowing for seamless integration with user-space tools and dashboards.
- Growing Ecosystem: eBPF has a growing ecosystem of tools and libraries, making it easier for developers and operators to leverage its capabilities. Some popular eBPF-related projects include Cilium, BPFTrace, bpftool, and many more.
How eBPF works?
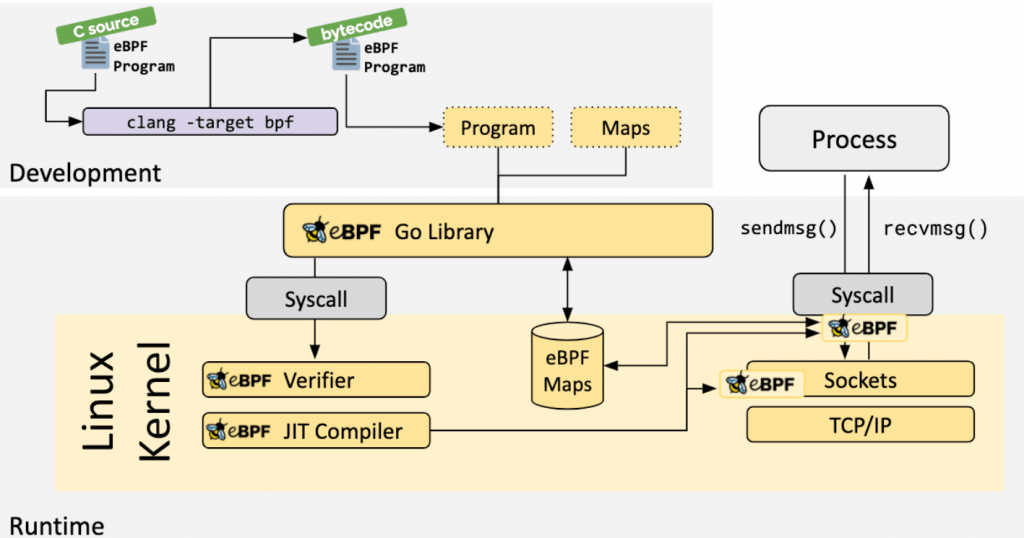
eBPF works by attaching programs to kernel events. These programs are compiled to bytecode, which is then interpreted by a virtual machine in the kernel. The virtual machine is sandboxed, so the eBPF program cannot access or modify any kernel memory or data structures.
eBPF programs can be used to implement a wide range of functionality, including:
- Observability: eBPF programs can be used to collect metrics and trace data from the kernel. This data can be used to troubleshoot performance problems, debug applications, and monitor system health.
- Security: eBPF programs can be used to implement security features such as firewalls, intrusion detection systems, and load balancers. It can also be used to isolate malicious processes and protect the system from attacks.
- Networking: eBPF programs can be used to implement custom networking features such as traffic shaping, load balancing, and filtering. It can also be used to improve the performance of existing networking protocols.
Here is a simplified overview of how eBPF works:
- The eBPF program is compiled to bytecode.
- The bytecode is loaded into the kernel.
- The eBPF program is attached to a kernel event.
- When the kernel event occurs, the eBPF program is executed.
- The eBPF program can collect data, perform calculations, and make decisions.
- The eBPF program can return data to the kernel or perform other actions.
Beginner’s Guide to eBPF
- What is Mobile Virtual Network Operator? - April 18, 2024
- What is Solr? - April 17, 2024
- Difference between UBUNTU and UBUNTU PRO - April 17, 2024

