
Linux Tutorials: Commands for Linux Administrator
1. sudo – Execute commands with elevated privileges, a fundamental for system administration. 2. useradd – Create a new user account, essential for managing user access. 3. usermod – Modify…
Read more »
Linux Tutorials: How to troubleshoot Linux Server?
If a linux-build-server suddenly starts getting slow, I would divide my approach / troubleshooting into 3 section as follows; System Level troubleshooting Application Level troubleshooting Dependent Services troubleshooting Understand Logs Level…
Read more »
Java Installation Guide in Linux & Windows
DOWNLOAD OPEN JDK & JRE JAVA PACKAGE FROM – https://jdk.java.net/archive/ Download and Install JDK/JRE 7 in Centos & RHEL Download and Install JDK/JRE 8 in Centos & RHEL Download and…
Read more »
Docker Tutorials: How to Install Docker in Ubuntu?
Install Docker Engine in Ubuntu NOTE – All commands you must run as root user or add a current user into a linux group name called “docker” How to beocme…
Read more »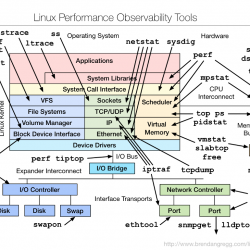
Linux Performance Monitoring Guide
CPU Memory Network Storage Device and Input I/O Storage Capacity Storage Controller CPU Memory and I/O Interconnect
Read more »
Linux Tutorials: mpstat commands examples
mpstat – Report processors related statistics. The mpstat command writes to standard output activities for each available processor, processor 0 being the first one. Global average activities among all processors…
Read more »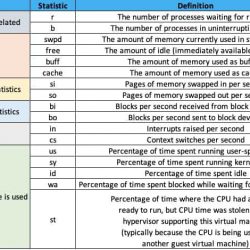
Linux Tutorials: vmstat commands examples
The vmstat command (short for virtual memory statistics) is a built-in monitoring utility in Linux. Users can observe system activity virtually in real-time by specifying a sampling period. The command…
Read more »
How to login linux server of AWS from windows using putty?
How to Generate PPK file from PEM using PuttyGen? AWS by default do not allow accessing a linux server using password so only key is allowed. But .pem file which…
Read more »
Installation and Configuration Guide: Bamboo
System requirements & considerations Java: Database: Installing Bamboo on Linux https://confluence.atlassian.com/bamboo/installing-bamboo-on-linux-289276792.html Install Bamboo using Docker Container Step 1 – Install Docker Step 2 – Install and Configure Bamboo using Docker…
Read more »Linux Tutorials: Commands for Linux User
ls – List directory contents. cd – Change the current directory pwd – Print the name of the current working directory. touch – Create an empty file or update the…
Read more »Top 50 Exim Interview Questions & Answer
1) You are not given the tools you need to be successful. How would you change that In Exim? State a business case to your manager / leader as to…
Read more »Top 50 traefik Interview Questions & Answer
1) What is Traefik software? Traefik (pronounced traffic) is a modern HTTP reverse proxy and load balancer that makes deploying microservices easy. Traefik integrates with your existing infrastructure components (Docker,…
Read more »
What is SELinux and how its SELinux used in Docker?
What is SELinux and how its SELinux used in Docker? SELinux, or Security-Enhanced Linux, is a part of the Linux security kernel that acts as a protective agent on servers. In the…
Read more »Top 50 Django interview questions and answers
1) Django design pattern? Django follows MVC pattern (Model-View-Controller), also referred to as MTV (Model-Template-View). Model – describes database schemaViews – Controls what user can view. It retrieves data from…
Read more »Top 50 WordPress interview questions and answers
1) What is WordPress? WordPress is an Open Source Content Management System (CMS) and a blogging tool, based on PHP and MySQL. It is free of cost, and you can…
Read more »Top 50 Apache HTTPD Interview questions and answers
1) What do you mean by Apache Web Server? Apache web server is the HTTP web server that is open source, and it is used for hosting the website. 2)…
Read more »Modules in Apache Web Server
Core Modules New functions are in the form of modules. Every module has their own directives Easy to download,install and configure Define modules, use their syntaxes to use that functions…
Read more »Directory Structure of Apache Web Server
Apache HTTPD – Directory Structure CORE/common Directories conf modules htdocs logs New structure in Yum/RPM base installation conf conf.d conf.modules.d modules htdocs logs Structure in Tarball/source code base installation conf…
Read more »Installation Of Apache HTTP Web Server
How many ways you can install Apache? Installation Types1.Yum Based2.RPM Based3.Source code/ Tar ball Based Apache install on Centos 7 (Yum Base) 1.Check OS version # cat /etc/*release 2.Install apache…
Read more »What is LAMP Stack?
What is Stack? The term stack(derived from “solution stack”) refers to a collection of different software programs that “stack” together to create a plateform necesary to support application software. These…
Read more »Best Practices of Linux Security
User Security Password Security Securing the root account File System Security System Security User Security Avoid shared accounts Ensure each user is assigned a unique account name and a unique…
Read more »Linux Security Tools
Vulnerability Assessment with Nessus Traffic Security with Ethereal Web Proxying with Squid Vulnerability Assessment with Nessus Nessus is a vulnerability assessment tool Comes built-in with most distros More than just…
Read more »How to Detecting and Stopping Attacks in Linux
System Auditing System Logging Network Intrusion Detection with Snort Host File Integrity with Tripwire System Auditing Auditing can track system activities to warn sysadmin of suspicious activity Allows sysadmin to…
Read more »Complete Referance of Secure Networking in Linux
OpenSSH Samba NIS NFS Securing FTP and HTTP servers OpenSSH Open source version of SSH that normally comes with OpenBSD Comes with several distros or downloadable Linux ports have ‘p’…
Read more »Complete Referance of Linux Security Mechanisms
TCP Wrappers etc/hosts allow and deny inted and xinetd PAMs SELinux Unsecure Linux Utilities TCP Wrappers TCP Wrappers is built into most distros Adds IP filtering capability Enables access logging…
Read more »Complete Referance of Firewalls in Linux Security
Introduction to Firewalls IP Tables Dedicated Linux Firewalls Introduction to Firewalls Firewalls protect network perimeters Not total security solution, but important part of defense in depth strategy Firewalls act as…
Read more »Complete Referance of Hardening in Linux Security
System Hardening Overview Batille Securing X-Windows Securing Linux Daemons Security patches Security Benchmarks System Hardening Overview Linux, like other operatingsystems, is not secure “out of the box” Security increases as…
Read more »Complete Referance of Encryption in Linux Security
Introduction to Encryption Using GNU GPG Using SSH Hashing Utilities Using PKI Certificates in Linux Introduction to Ecryption Linux has built-in ability to encrypt files Protects files in storage Protection…
Read more »Complete Referance of Linux Security
Course Outline Introduction To Linux Security A Bit About Linux Current Security Problems which is more secure: Windows vs Linux? Requirements of a Secure OS Overview of Linux Security Features…
Read more »
