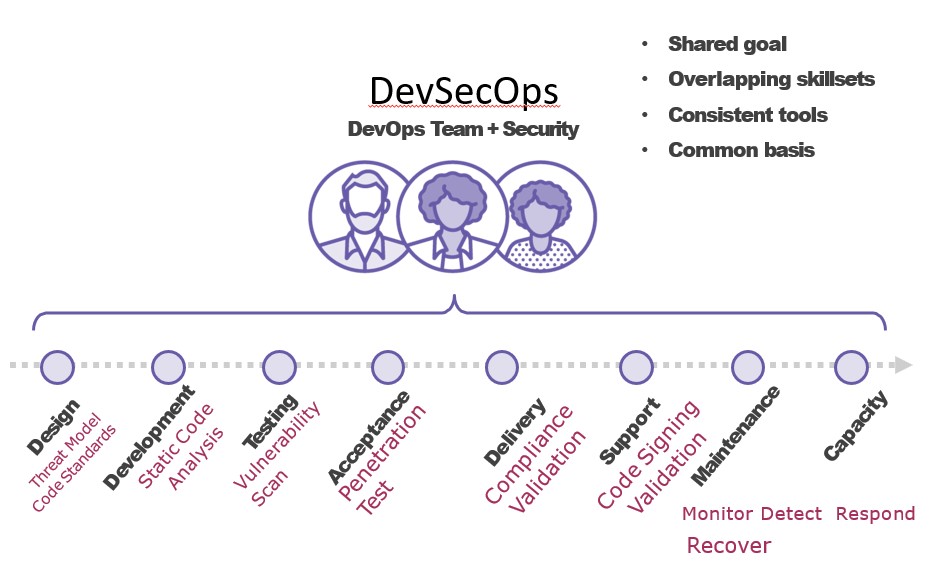
- Threat Model & Tools – STRIDE / PASTA / VAST & Microsoft Threat Modeling Tool / OWASP Threat Dragon
- Static Application Security Testing (SAST) – SonarQube
- Dynamic Application Security Testing (DAST) – OWASP ZAP (Zed Attack Proxy) / Skipfish / Nmap / OpenVAS by Greenbone / Fortify WebInspect
- Software Composition Analysis (SCA) – OWASP Dependency Check / Jfrog Xray
- Runtime application self-protection & Containers (RASP) – Falco / Notary / The Update Framework (TUF) / Nikto
- Web Application Firewall (WAF) – AWS WAF / Azure Web Application Firewall / Cloudflare Web Application Firewall (WAF)
- Securing Credentials – HashiCorp Vault & AWS Secrets Manager, Azure key vault, AWS KMS, Kubernetes Secrets
- Policy-based control for cloud native environments – Open Policy Agent (OPA)
- Infrastructure & Applications Security Testing, Auditing, Compliance, Scanners – Chef inspec
- Cloud Security service & Practices – Cloud Security with AWS & Azure service
- Security Information and Event Management SIEM – Splunk SIEM
OWASP SonarQube
OWASP SonarQube for Code Scanning. OWASP / SANS Security Reports. Dedicated reports let you track application security against known standard OWASP and SANS categories.
Chef InSpec
Chef InSpec for Scanning your applications and infrastructure. Chef InSpec is an open source (OSS) automated testing tool for integration, compliance, security, and other policy requirements.
ELK with Kibana
ELK with Kibana for Log analysis for Security Threat. “ELK” is the acronym for three open source projects: Elasticsearch, Logstash, and Kibana. Elasticsearch is a search and analytics engine. … Kibana lets users visualize data with charts and graphs in Elasticsearch. The Elastic Stack is the next evolution of the ELK Stack.
HashiCorp Vault
HashiCorp Vault for security tool for certificates, API keys, or passwords. Secure, store and tightly control access to tokens, passwords, certificates, encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API.
Fortify Webinspect
Fortify Webinspect for Dynamic Application Security Testing (DAST). Fortify WebInspect dynamic application security testing (DAST) software finds and prioritizes exploitable vulnerabilities in web applications.
Fortify Application Defender
Fortify Application Defender for Runtime Application Security Testing (RAST). Fortify Application Defender runtime application self-protection (RASP) protects production applications from common attacks and vulnerabilities.
AppScan on Cloud
AppScan on Cloud delivers a suite of security testing tools, including static, dynamic and interactive testing for web, mobile and open source software. It detects pervasive security vulnerabilities and facilitates remediation.
Twistlock
Understanding and Implementing Security aspect of Docker. Securing Hosts, Containers, and Serverless Across the DevSecOps Lifecycle. Trusted by more than 35% of the Fortune 100, Twistlock is the world’s first truly comprehensive cloud native security platform, providing holistic coverage across hosts, containers, and serverless computing in a single platform.
Notary
Understanding and Implementing Security aspect of Kubernetes. Notary is a core piece of plumbing in Docker’s approach to the secure supply chain whereby security is seamlessly and uniformly embedded into a workflow from development all the way through to operations. Notary is an implementation of The Update Framework (TUF) written in Go.
NewRelic
Understanding and Implementing Security aspect of Java Virtual Machine. leaders in the cloud security community, speaking at the Cloud Security Alliance, OWASP, RSA, and IAPP.
AWS Security service
Understanding and Implementing Security aspect of AWS cloud. Security, Identity, and Compliance on AWS. … AWS data protection services provide encryption and key management and threat detection that continuously monitors and protects your accounts and workloads. AWS Identity Services enable you to securely manage identities, resources, and permissions at scale.
ThreatModeler
ThreatModeler Cloud Edition automatically builds threat models for cloud infrastructures, managing potential threats for AWS and Azure environments. Our out-of-the-box cloud security solution provides an understanding of organizations’ entire attack surface and empowers enterprises to manage their risks more effectively.
Checkmarx
Flexible and accurate security solution capable of identifying hundreds of vulnerabilities. Supports over 22 coding and scripting languages and frameworks.
Trend Micro Cloud One
Detection and protection for modern applications and APIs built on your container, serverless, and other computing platforms.
Aqua Security
Full dev-to-prod container security solution on Kubernetes, Docker, OpenShift, Fargate, Lambda, AWS & other container platforms.
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I have worked at Cotocus. I share tech blog at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at TrueReviewNow , and SEO strategies at Wizbrand.
Do you want to learn Quantum Computing?
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at WIZBRAND
Find Trusted Cardiac Hospitals
Compare heart hospitals by city and services — all in one place.
Explore Hospitals
