Authentication – How to login into Jenkins
Authorization – User’s permissions to do in Jenkins
How to login into Jenkins or supported authentication methods in jenkins?
- Delegate to servlet container
- ‘Jenkins’ own user database
- LDAP
- Unix user/group database
- None
How to set user’s permissions for setting up required access in Jenkins?
- Anyone can do anything
- Legacy mode
- Logged-in users can do anything
- Matrix-based security
- Project-based Matrix Authorization Strategy
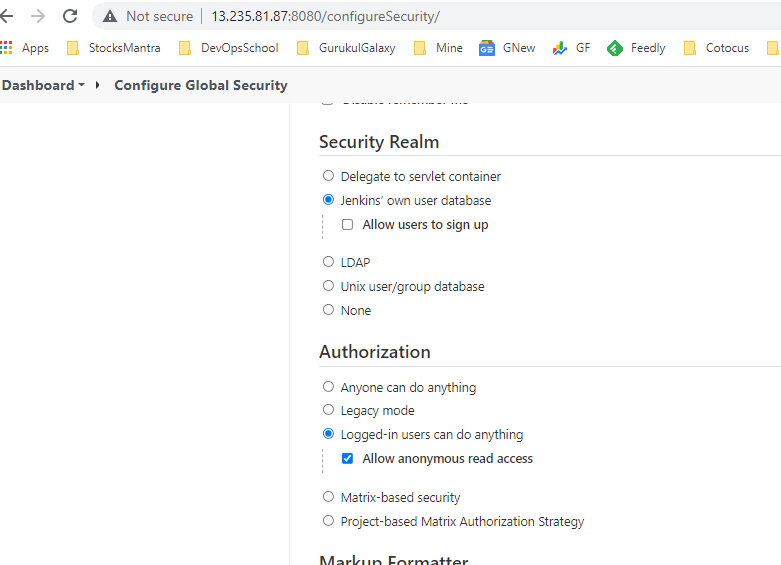
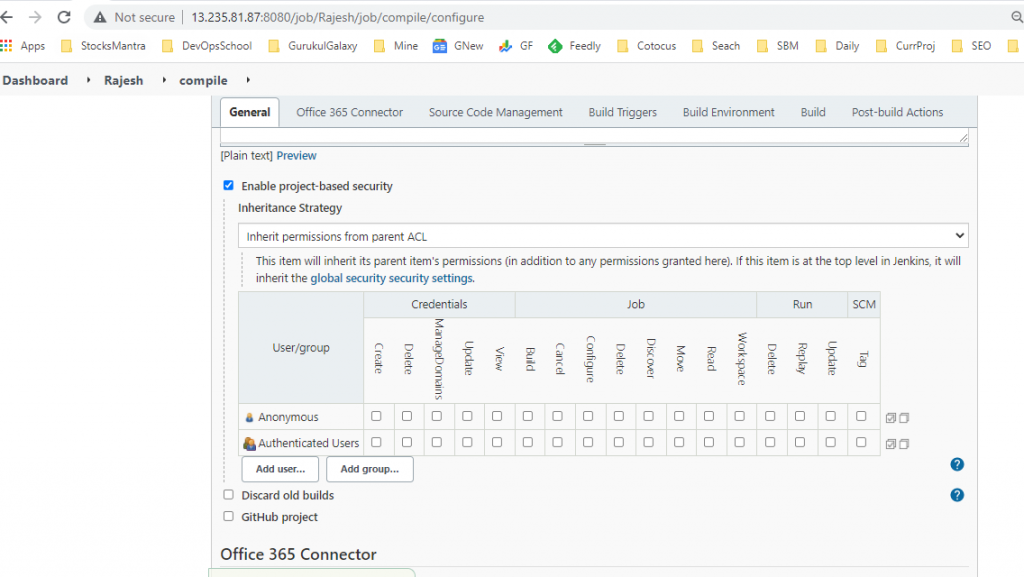
Matrix-based security
In this scheme, you can configure who can do what by using a big table.
Each column represents a permission. Hover the mouse over the permission names to get more information about what they represent.
Each row represents a user or a group (often called ‘role’, depending on the security realm.) This includes a special user ‘anonymous’, which represents unauthenticated users, as well as ‘authenticated’, which represents all authenticated users (IOW, everyone except anonymous users.) Use the text box below the table to add new users/groups/roles to the table, and click the [x] icon to remove it from the table.
Permissions are additive. That is, if an user X is in group A, B, and C, then the permissions that this user actually has are the union of all permissions given to X, A, B, C, and anonymous.
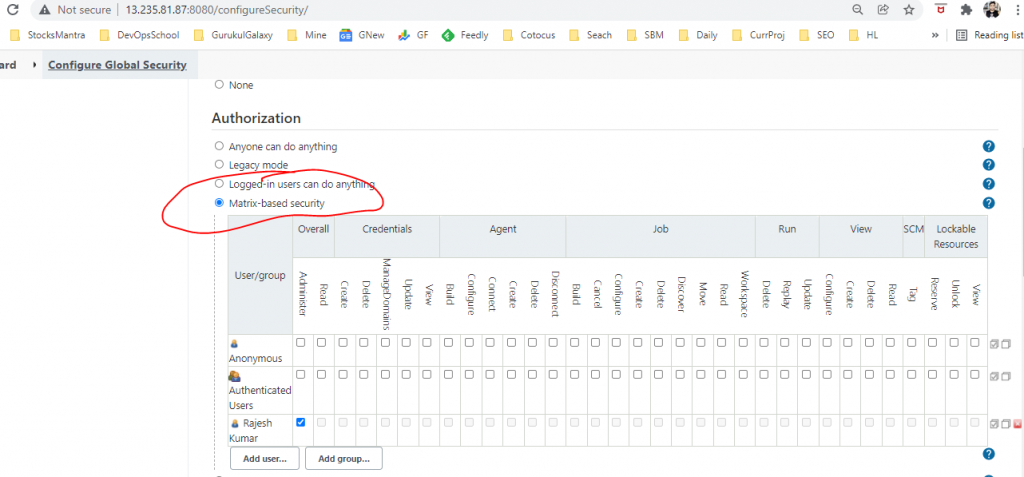
Project-based Matrix Authorization Strategy
This mode is an extension to “Matrix-based security” that allows additional ACL matrix to be defined for each project separately (which is done on the job configuration screen.)
This allows you to say things like “Joe can access project A, B, and C but he can’t see D.” See the help of “Matrix-based security” for the concept of matrix-based security in general.
ACLs are additive, so the access rights granted below will be effective for all the projects.
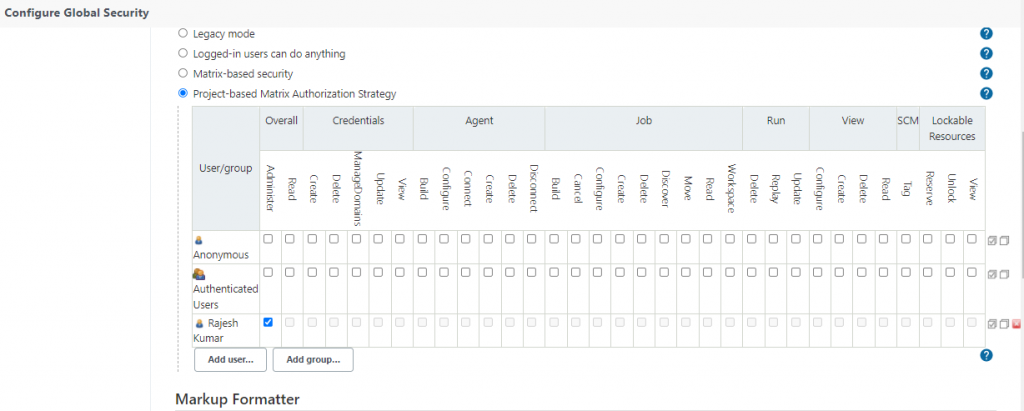
Project-based Matrix Authorization Strategy – Folder Level Access
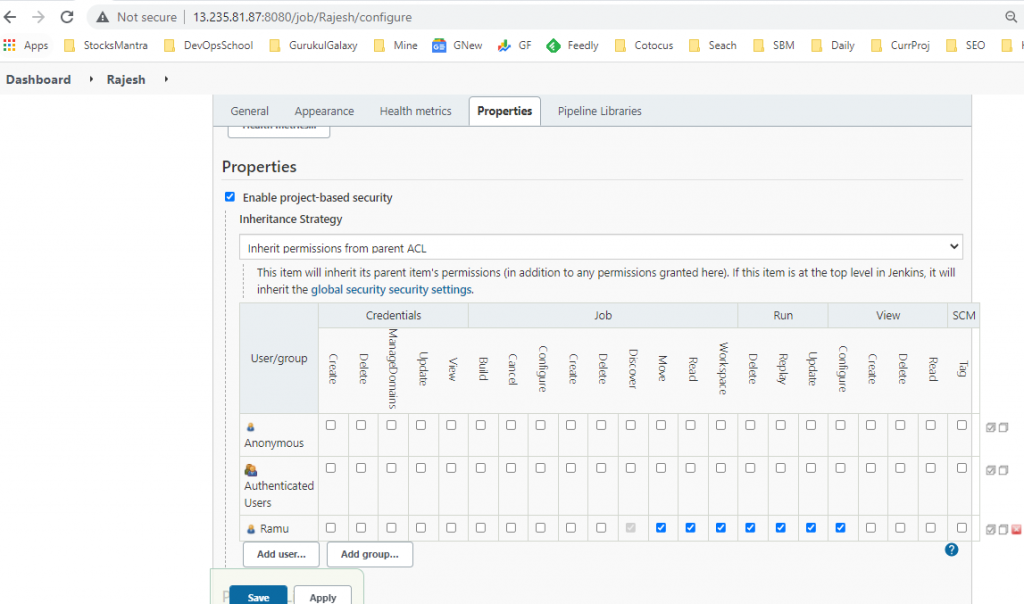
Project-based Matrix Authorization Strategy – Job Level Access
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I have worked at Cotocus. I share tech blog at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at TrueReviewNow , and SEO strategies at Wizbrand.
Do you want to learn Quantum Computing?
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at WIZBRAND
Find Trusted Cardiac Hospitals
Compare heart hospitals by city and services — all in one place.
Explore Hospitals
