Authentication mechanisms are modules that authenticate the user with a specific challenge or authentication technology, such as user name and password and one-time password. The order on which the authentication mechanisms are run is controlled by an authentication policy. Passwords are the most common methods of authentication. Passwords can be in the form of a string of letters, numbers, or special characters.
Top 10 Authentication mechanisms supported for applications in 2022
- HTTP Basic
- HTTP Digest
- HTTP NTLM
- Form based
- Authentication header
- OAuth
- OpenID
- SAML
- Google SSO
- Kerberos
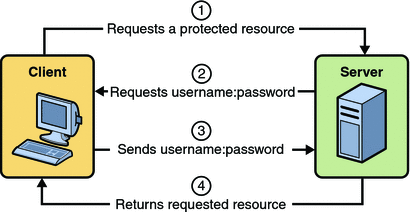
HTTP Basic
HTTP basic authentication is a simple challenge and response mechanism with which a server can request authentication information (a user ID and password) from a client. The client passes the authentication information to the server in an Authorization header. The authentication information is in base-64 encoding. Authentication is the process of identifying whether a client is eligible to access a resource. The HTTP protocol supports authentication as a means of negotiating access to a secure resource. The initial request from a client is typically an anonymous request, not containing any authentication information.
HTTP Digest
Digest authentication is another authentication type specified in HTTP 1.1. Unlike basic authentication, digest authentication does not require the password to be transmitted. Rather, the client takes the username and password and uses the MD5 hashing algorithm to create a hash, which is then sent to the SQL Server. Digest Authentication communicates credentials in an encrypted form by applying a hash function to: the username, the password, a server supplied nonce value, the HTTP method and the requested URI. Whereas Basic Authentication uses non-encrypted base64 encoding.

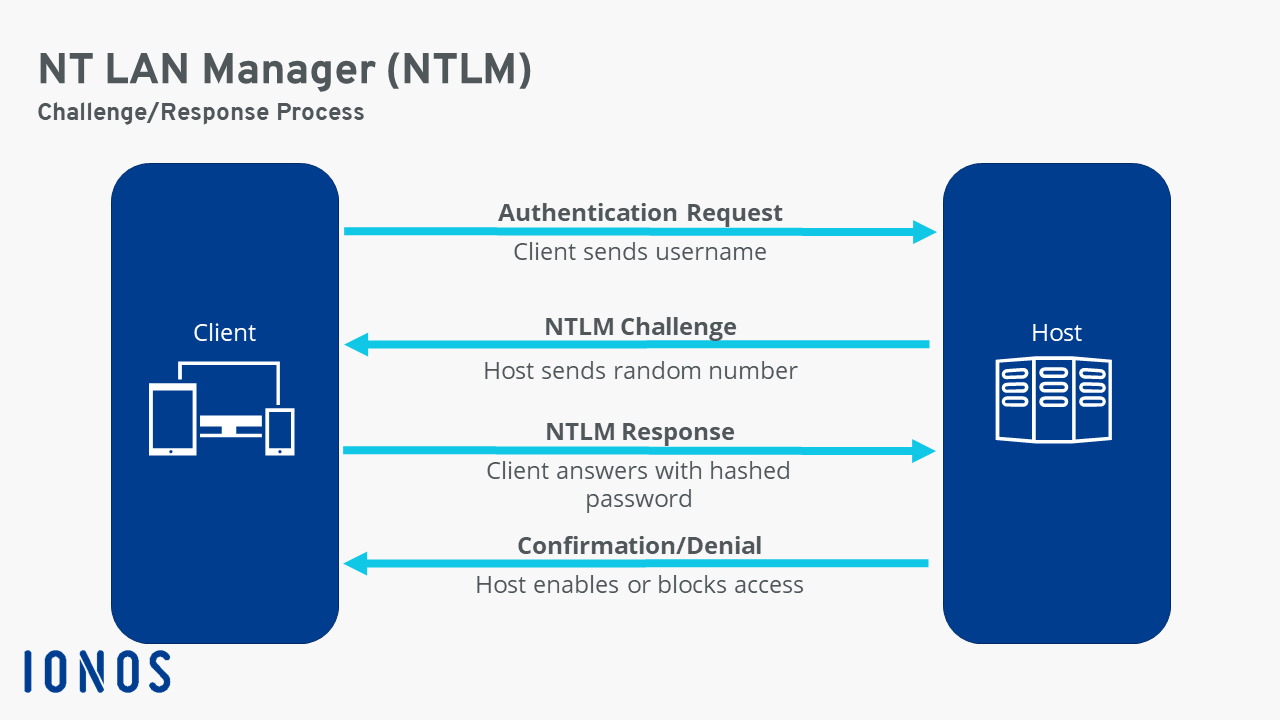
HTTP NTLM
NT LAN Manager (NTLM) authentication is a challenge-response scheme that is a securer variation of Digest authentication. NTLM uses Windows credentials to transform the challenge data instead of the unencoded user name and password. NTLM authentication requires multiple exchanges between the client and server. NTLM uses an encrypted challenge/response protocol to authenticate a user without sending the user’s password over the wire. Instead, the system requesting authentication must perform a calculation that proves it has access to the secured NTLM credentials.
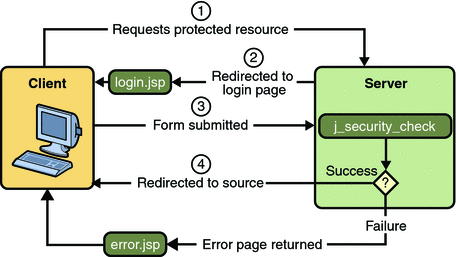
Form based
Form-based authentication allows the developer to control the look and feel of the login authentication screens by customizing the login screen and error pages that an HTTP browser presents to the end user. Form-based authentication is not particularly secure. In form-based authentication, the content of the user dialog box is sent as plain text, and the target server is not authenticated. This form of authentication can expose your user names and passwords unless all connections are over SSL.
Authentication header
The HTTP Authorization request header can be used to provide credentials that authenticate a user agent with a server, allowing access to a protected resource. The Authorization header is usually, but not always, sent after the user agent first attempts to request a protected resource without credentials. It is a simple authentication scheme built into the HTTP protocol. The client sends HTTP requests with the Authorization header that contains the word Basic, followed by a space and a base64-encoded(non-encrypted) string username: password. For example, to authorize as username / Pa$$w0rd the client would send.
OAuth
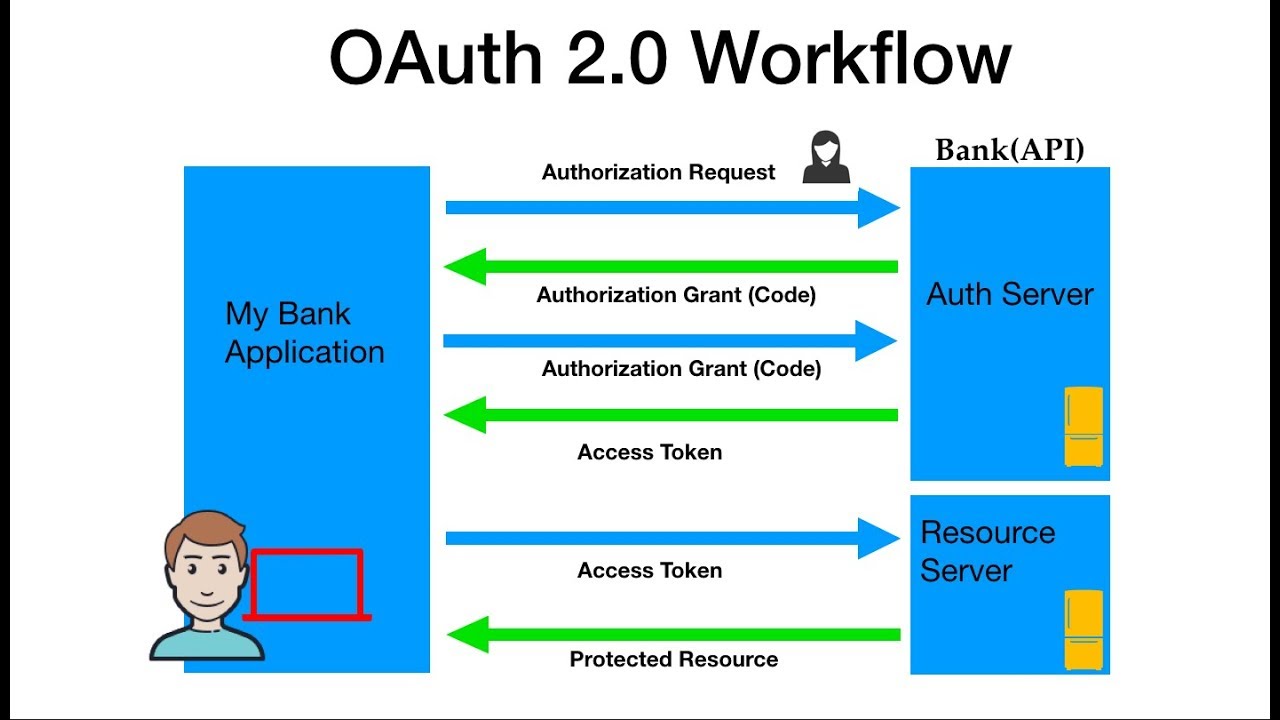
OAuth is an authentication protocol that allows you to approve one application interacting with another on your behalf without giving away your password. OAuth is an authorization framework that enables an application or service to obtain limited access to a protected HTTP resource. To use REST APIs with OAuth in Oracle Integration, you need to register your Oracle Integration instance as a trusted application in Oracle Identity Cloud Service.
OpenID
OpenID Connect (OIDC) is an open authentication protocol that profiles and extends OAuth 2.0 to add an identity layer. OIDC allows clients to confirm an end user’s identity using authentication by an authorization server. OpenID allows you to use an existing account to sign in to multiple websites, without needing to create new passwords. You may choose to associate information with your OpenID that can be shared with the websites you visit, such as a name or email address.

SAML
SAML authentication is the process of verifying the user’s identity and credentials (password, two-factor authentication, etc.). SAML authorization tells the service provider what access to grant the authenticated user. The browser passes SAML request to the identity provider. The identity provider parses the SAML request. The identity provider authenticates the user by prompting for a username and password or some other authentication factor. NOTE: The identity provider will skip this step if the user is already authenticated. As SAML is a standard protocol, it can be used in any application in spite of the implementation. Being standardized SAML prevents interoperability issues in between applications when exchanging information. SAML provides a single point of authentication, where every user is authenticated at the identity provider.

Google SSO
You can configure your Cloud Identity or Google Workspace account to use single sign-on (SSO). When you enable SSO, users aren’t prompted to enter a password when they try to access Google services. Instead, they are redirected to an external identity provider (IdP) to authenticate.

Kerberos
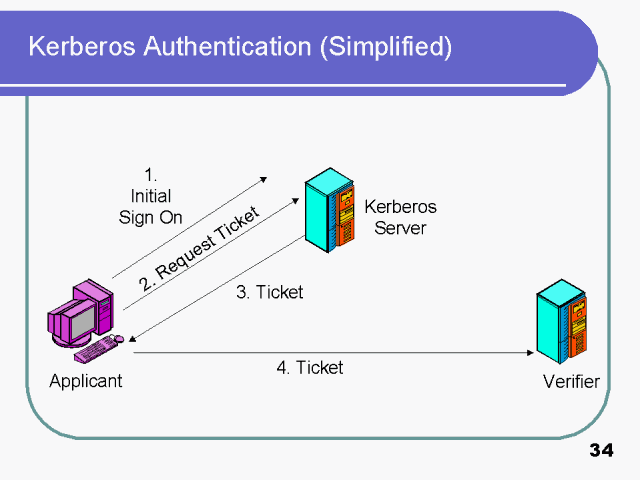
Kerberos authentication is a multistep process that consists of the following components: The client who initiates the need for a service request on the user’s behalf. The server, which hosts the service that the user needs access to. The AS, which performs client authentication. Kerberos provides a centralized authentication server whose function is to authenticate users to servers and servers to users. In Kerberos Authentication server and database is used for client authentication. Kerberos runs as a third-party trusted server known as the Key Distribution Center (KDC).
- How to become a devops freelancer - July 15, 2023
- DevOps Support Services Market in India - July 15, 2023
- 5 Key Considerations Before Embarking on An App Development Project - July 14, 2023

